Unlocking the Fortress: A Comprehensive Guide to Secure Network Systems Design

In today's interconnected digital landscape, securing network systems has become paramount. Breaches and cyberattacks can have devastating consequences for businesses, organizations, and individuals alike. "Principles of Secure Network Systems Design" is the definitive resource for IT professionals, network engineers, and security architects seeking to establish robust and impenetrable network defenses.
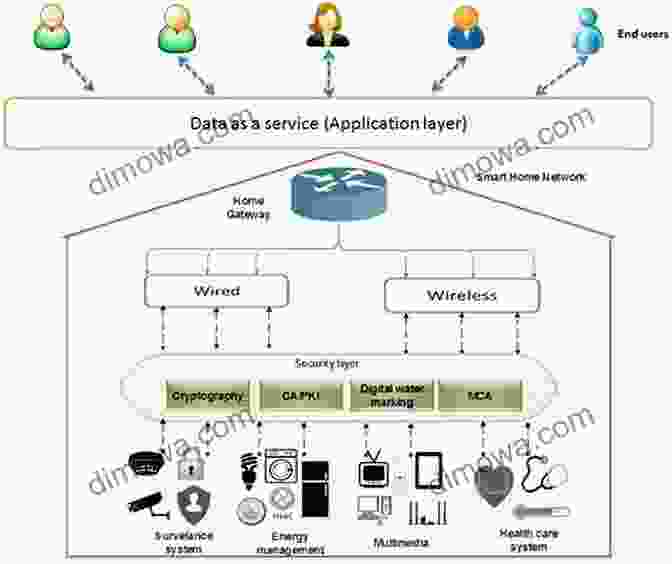
Unveiling the Framework for Secure Network Systems
This comprehensive book provides a step-by-step guide to designing, implementing, and maintaining secure network systems. It introduces a structured framework that encompasses:
4.7 out of 5
| Language | : | English |
| File size | : | 3968 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Print length | : | 235 pages |
- Risk Assessment and Analysis: Identifying vulnerabilities and potential threats.
- Network Architecture Design: Implementing secure network topologies and segmentation.
- Security Controls Deployment: Implementing firewalls, intrusion detection systems, and encryption technologies.
- Policy Development and Enforcement: Establishing clear security policies and procedures.
- Continuous Monitoring and Auditing: Detecting and responding to security incidents promptly.
In-Depth Coverage of Network Security Technologies
The book delves into the latest network security technologies and best practices, including:
- Virtual Private Networks (VPNs): Securing remote access and data transmission.
- Network Access Control (NAC): Restricting network access to authorized users and devices.
- Intrusion Detection and Prevention Systems (IDS/IPS): Detecting and blocking malicious network activity.
- Web Application Firewalls (WAFs): Protecting web-based applications from attacks.
- Cloud Security: Securing network systems deployed in cloud environments.
Practical Examples and Case Studies
"Principles of Secure Network Systems Design" is not just a theoretical guide but also a practical resource. It includes:
- Real-world examples: Illustrating the application of secure network design principles.
- Detailed case studies: Showcasing the implementation of secure network systems in different scenarios.
- Interactive exercises: Engaging readers in hands-on learning and assessment.
Expert Insights and Best Practices
Written by industry-leading security professionals, the book distills decades of experience and best practices. It provides invaluable insights into:
- Cybersecurity Trends: Identifying emerging threats and vulnerabilities.
- Compliance and Regulatory Requirements: Meeting industry standards and government regulations.
- Security Testing and Evaluation: Assessing the effectiveness of network security measures.
Empowerment for IT Professionals
"Principles of Secure Network Systems Design" empowers IT professionals to:
- Enhance Security Posture: Build and maintain highly secure network systems.
- Mitigate Risks: Identify and mitigate vulnerabilities before they become threats.
- Protect Sensitive Data: Safeguard critical information from unauthorized access and theft.
- Ensure Compliance: Adhere to regulatory and industry standards for network security.
- Advance Career Prospects: Become highly skilled and sought-after in the field of network security.
"Principles of Secure Network Systems Design" is an indispensable guide for anyone seeking to protect their network infrastructure. Its comprehensive coverage, practical examples, and expert insights provide the knowledge and tools necessary to build and maintain robust and impenetrable network defenses. By investing in this book, IT professionals can elevate their skills, safeguard their systems, and protect their organizations from the ever-evolving threats of the digital age.
4.7 out of 5
| Language | : | English |
| File size | : | 3968 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Print length | : | 235 pages |
Do you want to contribute by writing guest posts on this blog?
Please contact us and send us a resume of previous articles that you have written.
 Book
Book Novel
Novel Page
Page Chapter
Chapter Text
Text Story
Story Genre
Genre Reader
Reader Library
Library Paperback
Paperback E-book
E-book Magazine
Magazine Newspaper
Newspaper Paragraph
Paragraph Sentence
Sentence Bookmark
Bookmark Shelf
Shelf Glossary
Glossary Bibliography
Bibliography Foreword
Foreword Preface
Preface Synopsis
Synopsis Annotation
Annotation Footnote
Footnote Manuscript
Manuscript Scroll
Scroll Codex
Codex Tome
Tome Bestseller
Bestseller Classics
Classics Library card
Library card Narrative
Narrative Biography
Biography Autobiography
Autobiography Memoir
Memoir Reference
Reference Encyclopedia
Encyclopedia Miyoshi Tomori
Miyoshi Tomori Cidney Swanson
Cidney Swanson Winfred Peppinck
Winfred Peppinck Deanna Kinney
Deanna Kinney Thomas F Homer Dixon
Thomas F Homer Dixon Arthur Schopenhauer
Arthur Schopenhauer Oliver Phipps
Oliver Phipps Tim Hopgood
Tim Hopgood Kellie Hailes
Kellie Hailes Mikey Brooks
Mikey Brooks Tom Savage
Tom Savage Stephanie Albright
Stephanie Albright Jessica Eissfeldt
Jessica Eissfeldt Robert James Waller
Robert James Waller Senka Lazarevic Reynolds
Senka Lazarevic Reynolds Thomas Monahan
Thomas Monahan D C Robinson
D C Robinson Louise Chipley Slavicek
Louise Chipley Slavicek Mike Ormsby
Mike Ormsby Swan Aung
Swan Aung
Light bulbAdvertise smarter! Our strategic ad space ensures maximum exposure. Reserve your spot today!

 John GrishamGeometric Integration Theory Cornerstones: Your Guide to Differential Forms,...
John GrishamGeometric Integration Theory Cornerstones: Your Guide to Differential Forms,... Brian WestFollow ·13.3k
Brian WestFollow ·13.3k Ken FollettFollow ·18.1k
Ken FollettFollow ·18.1k Henry JamesFollow ·13.4k
Henry JamesFollow ·13.4k Guillermo BlairFollow ·8.2k
Guillermo BlairFollow ·8.2k Lord ByronFollow ·17.1k
Lord ByronFollow ·17.1k Hector BlairFollow ·9.6k
Hector BlairFollow ·9.6k Dallas TurnerFollow ·2.5k
Dallas TurnerFollow ·2.5k Barry BryantFollow ·14.2k
Barry BryantFollow ·14.2k

 F. Scott Fitzgerald
F. Scott FitzgeraldLove Me Better, Love Me Right: A Journey of...
Unveiling the Profound Power of Emotional...

 Eddie Powell
Eddie PowellHow To Make Your Muzzleloader Most Effective And Keep It...
In the realm of firearms, muzzleloaders hold...

 Andy Hayes
Andy HayesPrepare Mentally, Physically, and Emotionally for the...
Embark on a Transformative Odyssey to...

 Oliver Foster
Oliver FosterThe Bittersweet Bride: Advertisements for Love
A Poignant...
4.7 out of 5
| Language | : | English |
| File size | : | 3968 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Print length | : | 235 pages |